I was asked by a client to write up a brief (Ha!) email to send to their staff to help them better recognize what the difference is between safe emails and unsafe emails. The amount of ransomware infections going on across business in this country right now had them concerned and rightfully so! I decided we'd post it here as a blog post so all our clients could see the information. And I apologize in advance for anyone that thinks this might be a BRIEF conversation.
What's the big deal?
We live and work in a digital world that is vastly different from the one ten years ago. A decade ago email was simply a method of communicating information more efficiently than postal mail. As it became adopted into mainstream business it became a way to vastly increase the speed at which we can get things done. Insurance records can be transferred in real-time. Customer support can be handled almost instantly from thousands of miles away. Patient records can be communicated between doctors at a speed that routinely saves lives. The benefits of having instant communications via email are incredible.
It is, however, also an avenue of attack on personal and business computers that is being utilized more and more each passing day.
The proliferation of ransomware has made electronic mail even more dangerous that it already was. Ten years ago, it was relatively simple to stop viruses at the desktop level. To oversimplify it a little it works like this:
- Someone, either accidentally or intentionally, sends you an infected email.
- Your virus software catches it and stops you from opening it.
Easy huh?
What changed?
A lot of things have changed.
- Fake emails have become MUCH more authentic in appearance than they used to be.
- They are no longer simply infected attachments, but are more often phishing scams - emails that LOOK real enough to get you to click on a link to visit something you think is a legitimate site.
- They are backed up by incredibly realistic looking fake websites.
- Hackers and companies and rogue individuals are making LOTS of money using ransomware to hold computers hostage. As long as it remains a profitable enterprise it will only get worse.
What protections should you use?
There are a number of things you, as a computer user, can do both at home and at work to minimize your risk of getting infected.
- Use a mail service that has built-in antivirus (Yahoo mail and many of the free ones do not. Our Exchange mail service has this built-in.)
- Use a web filter (We offer a service like this for our both residential and business customers).
- Use antivirus software on your computer.
- Update your antivirus often! (Our managed antivirus customers update every hour already, so they're already protected.)
- Disable automatic preview of emails.
- Disable images in emails from unknown sources.
- Scrutinize emails before you open them.
The last one is still the most important. If you have EVERY OTHER step above properly addressed, infected emails can still slip through. Failing to pay close attention to what emails you open and what links you click on is the part most people assume they don't have to do. After all - they have antivirus software. They paid for that, right? That's what its there for?
Let me use an analogy: You might have gotten the flu shot this year right? Do you feel safe walking through an ebola-infected village just for the fun of it? Of course not. That's crazy! The same premise should apply to the use of electronic mail.
Here is an example from my own email, received a few weeks ago:
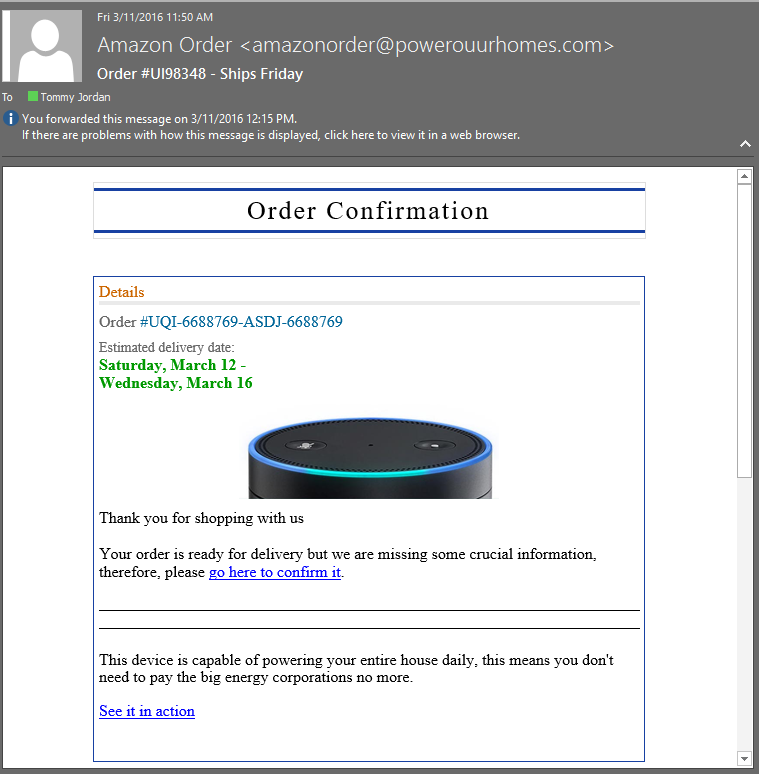
Fake phishing email from "Amazon"
That image above appears to be from Amazon. As a big-time user of Amazon I actually DO have an Amazon Echo, so when I got an email from them confirming my order I almost clicked the link to see what was going on. After all, I have an Echo, but I hadn't ordered another one. I didn't want to be charged for a second $179.00 unit! My frustration almost convinced me to click the links in the email before I considered what was happening.
Now, I shop from Amazon a LOT. No, seriously, a lot! Like I need a support-group alot. Ok?
This is what an authentic amazon email looks like:
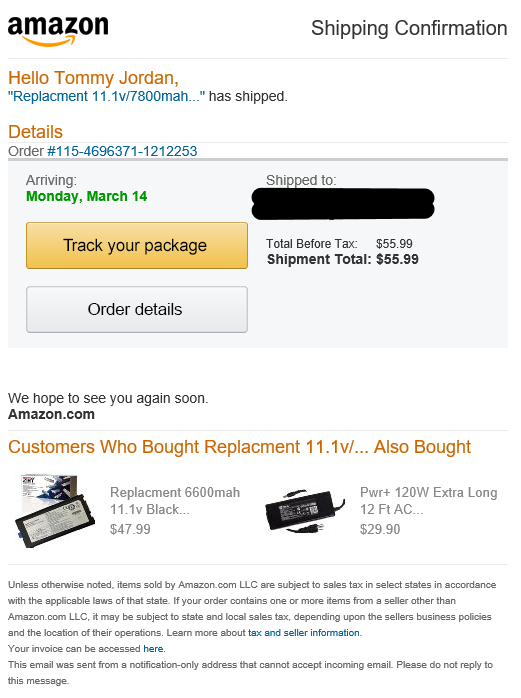
Something made me pause and examine the links before I clicked on them. When I compared it to a real amazon email, the differences were obvious, so I didn't click on anything in the email. However, if this were sent to my 66-year-old mother there is a good chance she would have clicked the link and been directed to an infected site.
There's something worth noting here. See that list of 7 items above that I said you should do? I have ALL of those protections on my work computer and that email still got through. Thankfully it wasn't a ransomware infection. It was a much more simplistic phishing email linked to an infected website, but the reality would be the same if it had been ransomware.
Antivirus will NOT protect you against ransomware. End of story. Period. It's incredibly important that you understand that point. No antivirus platform out there right now protects against ransomware or cryptoware. These are a new breed of infection that isn't really a virus at all.
What is ransomware and cryptoware?
It might be important for you to know the difference between these threats and a normal virus, so we'll cover the differences briefly.
A virus (most of them anyway) causes you minor inconvenience. They're an annoyance. They might cause popups to display when you're browsing the internet. They might change your homepage. They might send spam to your friends on Yahoo by infecting your email when you login or your Facebook account when you login. They might steal your banking credentials.
These are all a real pain, but they're all correctable almost immediately with help from a professional.
Cryptoware and Ransomare act differently.
- They usually stay cloaked for awhile; anywhere from a few hours to a few weeks.
- While they're cloaked and your antivirus software isn't aware of them, they search through your computers and anything connected to it on your network including flash drives, other computers, portable hard drives, etc.
- They make a list of every single kind of file they can find to infect. This includes all documents, spreadsheets, databases, power points, PDFs, images, text files, and any other common document format they can possibly get their hands on.
- They slowly start encrpyting them - making them unreadable and useless to you. (It's important to note that this isn't a virus activity. This is something you could do yourself, so your antivirus software isn't going to register the activity.)
- They remain hidden awhile longer - just to be sure they've had a chance to infect any backup files you might have. If you run a weekly backup, that's useless if the ransomware has been sitting in your system for three weeks silently infecting both your native files and your backup files.
- THEN they announce themselves. Hey! You're infected and you can only get your data back if you pay us to access it!
What does a ransomware infection look like?
Here are a couple examples of some of the more common versions out there today.
This is cryptolocker. It's fairly common. It tells you you have x amount of hours or days to pay the ransom or your files will be forever locked away.
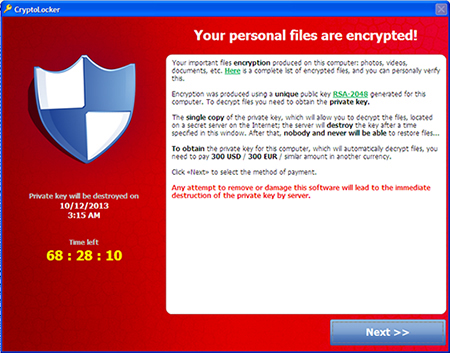
This is Locky - a new breed of ransomware that's been out lately. It basically does the same thing; locking up your files unless you pay the authors in bitcoin. The cost has been anywhere from $400 to $2,000,000 in recent news.
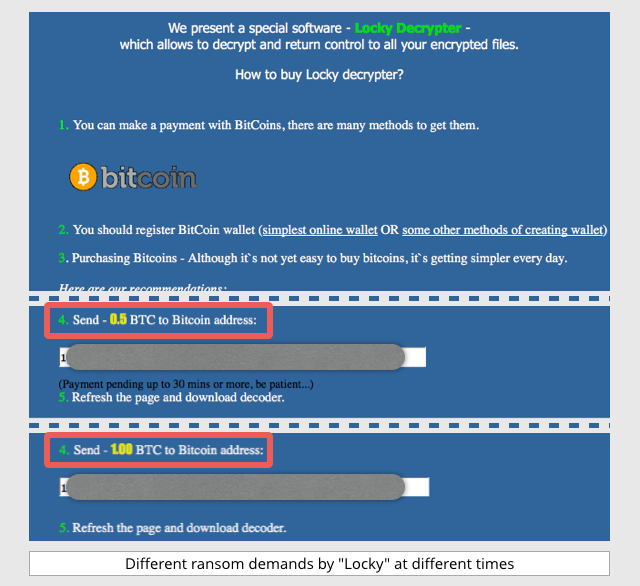
What happens if we get infected?
If your home computer gets infected with ransomware there is a good chance you can kiss all those baby pictures good-bye unless you have a non-connected backup somewhere in a safe that hasn't been connected to a computer since before you got infected. Let's be honest with ourselves - how many of us really have that?
If your work computer gets infected, the scale of damage becomes monolithic. It's not even an easy matter to calculate the damage it would cost your company, but here are a few things that come to mind:
- Every computer on your network has to be wiped - completely wiped of all data and everything has to be reinstalled from scratch. The mere chance that an infection could remain behind and require the process to be done all over is too high, so everything has to go. In our industry we call this last resort "Nuke and Pave" and it's as drastic as it sounds. It equates to the idea of dropping a nuclear bomb on your network, killing everything, and the repaving with a clean slate. Nuke and Pave is NOT a phrase you ever want to hear from your IT guy in a meeting. Seriuosly... ever. EVER!
- ALL your data was lost. Every document, every client file, every accounting ledger, every patient in your medical database (depending on its format) will have to be recreated.
- Your business will be down while this happens. After all, how many companies out there in major industries can work with no computers whatsoever?
- Your owners and staff will be trying the best they can to answer phones and explain to clients that you've been hacked/breached/blocked and all your data is gone. After all, if you maintain personally identifiable information on your computers that could be used to reconstitute an identity, you're required by federal law to inform all your customers ASAP. The same holds true if you have their credit card numbers. You're on the hook to inform them immediately so they can try to mitigate any damages from stolen cards, etc. (Wait, have you thought how you're going to call all your customers if you don't have access to your client data? That'll be fun, huh?)
If you have 25 computers, it would be a safe estimate to say you'd be completely dead in the water for 3 to 4 days minimum. Realistically, I know our customer base forward and backward and if it were one of the firms we have with 25-30 computers, it would likely take a week or more.
It would take that long just to get all your computers wiped and reinstalled and your network set up from scratch again. Then we have to begin the painstaking process of trying to restore files that most likely can't be easily restored, if at all. Let's assume the bill from your IT company would be a conservative $100 an hour (and I can assure you that's on the low end.) You could expect a constant $300-$500 an hour non-stop for days just to get to your data and try to recover it. That's on top of the bill they just gave you to completely rebuild your entire company overnight for three or four nights straight.
One of our companies is an insurance broker with over 300,000 around a week just to get that data, maybe up to a month, and could feasibly cost $25,000-$50,000 just in data recovery if they weren't adequately protected.
Long story short:
- It will cost your company a lot of money.
- It will cost your company customers. If you suffer a data breach like that, you WILL lose customers. It's a fact.
- It will cost your company a tremendous waste of employee hours. After all, we need your staff there to assist us locating your data, resetting preferences, etc.
- It will cost you downtime. Ever thought about closing your doors and going on vacation for a week? Of course not. You have clients that need you. You might as well consider going on vacation for a week. At least you'd get to enjoy a margarita during your own personal trip through hell!
What to look for to protect yourself
Remember, antivirus alone will NOT stop any of the major forms of ransomware or cryptoware!
Now that we have hopefully impressed upon you the severity of this threat - and make no mistake - there is NO GREATER THREAT to businesses today than that of cyber-attack via these tools, let's see if we can give you some tips and tricks to stay as safe as possible.
Tips to stay safe using email
Banking/Financial Emails
Know that no banking institution will EVER send you attachments in email to open as part of some important information regarding your account. If you think you have an important update from your bank, login to the banking website by typing in the address in your browser, and look for it in your message section, or in bold red on top of the page after you login. Do NOT click on a link in an email.
If you don't bank with the institution that just sent you an email, such as Bank of America when you bank at Wells Fargo, then they did NOT email you. It's spam, phishing, or an infection, so delete it.
Email from the Federal government
No Federal agency (IRS, etc) will ever send you attachments or require you to click encrypted links in an email. In fact, that IRS doesn't use email to communicate with taxpayers at all, ever, so you can safely ignore anything that looks like that.
Random links
If it's a personal email that contains a link and you weren't expecting something like that from that person - call them and ask about it. Be sure they sent it. You can even email them and ask about, but compose a new email. DO NOT REPLY to the one you're suspicious of. It could be a "spoofed" email - a person pretending to be someone they're not.
Grammar and word choice
Watch out for funny or non-standard wording in emails. Scroll up and look at the amazon example from before. If you read the contents of the message the last sentence says:
"This device is capable of powering your house daily, this means you don't need to pay the big energy corporations no more."
Does that horrible grammar, poor word choice, and overall structure stand out to you? It should. That is NOT something you'd expect to see in an email from Amazon. The clue often lies in word choice.
Many of these kinds of scams come from other countries where the grasp of English is decent, but not up to conversational norms. As such, some words or phrases will sound off-key. Don't trust those emails.
Another key identifier that will 100% guarantee it's spam or phishing is the addition of paragraphs of non-related text at the bottom of an email. You might have seen this and wondered why in the world they were there. They're there to trick the spam server into letting the email pass through. You might have received a spam email about finding the right insurance company, but all the extra text at the bottom tricks the spam server into saying "Wait, maybe this is legitimate communications after all" and allowing the email through. Here is an example of the text included at the bottom of the fake Amazon email earlier:
Don't enable inline images
Don't enable images unless you know the source. This one can be tricky, so let me explain: When you see an email preview that contains images you will usually see placeholders and a notice on the top of the email stating that images have been disabled. You can usually click that notice and choose to display images. If you aren't 150% confident you know the source, don't enable the images in the email. Images are often encoded with tracking information and can contain other nasty infections as well.
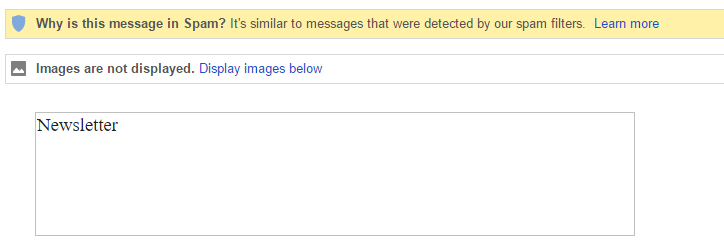
This is an example of what I'm talking about:
Notice the image above doesn't load? It just says Newsletter. I can click the "Display images below" if I really want to see it, but considering I don't know the company and it's not someone I do business with, I'd just read the email without any images.
Twisted Networx Exchange Email Users:
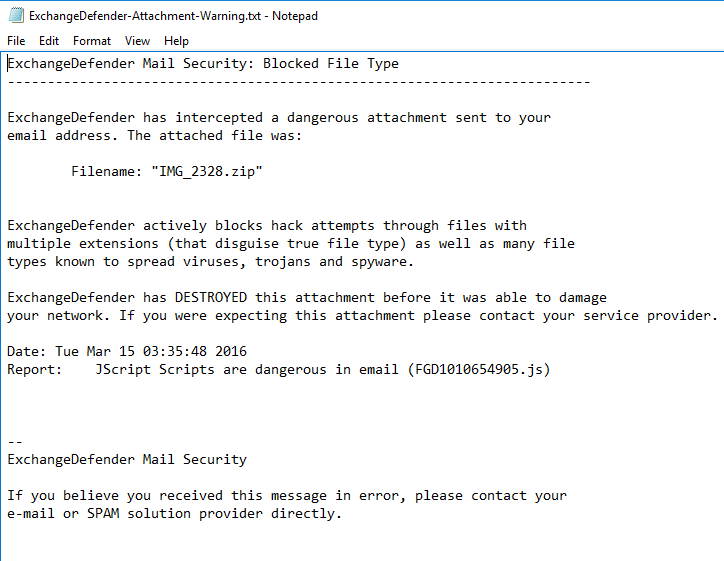
You have another level of protection in your email if you are one of our hosted Exchange customers. If you get an infected message that it recognizes contains a virus or trojan, our mail system will destroy it before it ever gets to you. You will get an email that says this:
Warning: This message has had one or more attachments removed Warning: (FGD1010654905.js, IMG_2328.zip). Warning: Please read the "ExchangeDefender-Attachment-Warning.txt" attachment(s) for more information.
That email will contain a text file attachment that ALWAYS has the same file name mentioned above.
You can just delete the email, or you can choose to read the text attachment if you want to find out more about the file and who sent it to you. The attachment looks like this:
Tips to stay safe on the web and social media?
Email and internet are the most obvious and most abused threat-vectors out there today. We've covered email as well as we can without offering a multi-hour online course I think, so we'll move on to social media and internet usage.
Most of our clients already have our internet web-filtering service in place, but I'll briefly cover what it does for the benefit of those that don't have it but might want it. It is a simple program (called an agent) that sits on the desktop or laptop of all your computers and:
- analyzes all traffic to and from the internet on the DNS layer.
- prevents you (or your employees, kids, etc) from visiting sites that we know are bad and that are already in our blacklists.
- prevents users from visiting sites you've determined they shouldn't be using (Social networking, gamlbing, porn, etc.)
- costs $5 per month per computer.
Assuming you don't have something like this in place, you have to rely on your own good judgement when considering what is and isn't safe on the internet. Here are some guidelines for the web and social media:
- Avoid clicking to sites from other sites that aren't known to you. If you need to go to Google, type google.com in your address bar. If you need to visit Facebook, type facebook.com in your address bar. If you don't know what your address bar is, just stop and get off the computer. None of the rest of this will make any sense to you. lol. The point is: don't click on a link on some other non-related site that offers to link you to Facebook. There's a good chance it's NOT Facebook you're going to.
- Don't click random links in people's twitter feed, Instagram feed, other other feed. People get hacked daily on social networks and the only purpose for that hack is usually to get others that know the person to click on the infected links.
- If a post from someone doesn't look like something they'd normally post, don't click on it. Don't comment on it. Just call them on the phone or email them and ask if it's legitimate. They might have been hacked and don't yet know it. This happens daily on Facebook.,
- Don't respond to messages that seem out of character or that talk about winning money. Chances are, they aren't really from your friend on Facebook. They're the result of them getting hacked and it's spam sent out to all their contacts.
- Don't have stupid passwords. We're dead serious on this. We hear all the time that "I can't remember hard passwords so I use my kid's name" or something equally asinine. How many hundreds of thousands of articles are there out there on password security? If you haven't bothered to listen to them yet, then it's likely too late.
- Don't have the same password for your social media or email that you do for anything else. Be sure your social media passwords are NOT the same as your email passwords and that NEITHER of those is the same as your banking passwords.
- Don't click on ads if you can get to it another way. If you see an ad on Facebook or some other site about a new deal from your insurance company, try to Google search the deal yourself. Don't click on the ads to get there. You can almost always find out what you want to know with a simple Google search just as easily.
- Don't click on product ads. If you see an ad for a kitchen appliance you like with an amazon link, just type Amazon.com in the address bar, go there yourself, and search for the item. The same goes for eBay.
- Stay off craigslist altogether. It's full of internet-nasty stuff.
- Stay off adult websites.
- Stay off Free Game Sites! (These are the worst for infecting your browser.) Here's a small fact - NO ONE invents games for people to play for free. No one. It's never happened. There is something else you're getting when you sign up to play those. It's usually some new toolbar that throws ads at you non-stop but it could very well be something more malicious.
- Don't ever use online coupon programs. They're one of the most highly-infected vectors out there on the internet.
Games and Coupons - Why are we harping on those?
The truth is that free online games and coupon discount websites attract a certain demographic. It's usually women. It's also usually women who are 40 or older. It's specifically successful amongst women that are retired or stay at home. More than any other demographic, retirees and non-employed individuals often spend more time looking for things to fill their time on the internet. This makes them a VERY attractive target to hackers and spammers. They're less likely to catch themselves before they're infected than an 18-year old techno-savvy computer user is before they get infected with something.
How can I prevent this kind of attack?
You probably can't. Sucks doesn't it?
Can you protect yourself and use all reasonable measures not to get infected? Yes.
Can you absolutely 100% guarantee you'll never get this kind of infection? Not unless you were either willing to invest a LOT of money into your backup infrastructure or were willing to get knocked back to the stone age and use air-gapped computers, which wont work in today's cloud-enabled world.
Seriously, I'll spend the money - what do I need to do?
There certainly are those of you out there that take this seriously enough to want to try everything reasonable to protect your business and the investment you've made in seeing it succeed. Those of you that have personal computers - just stop reading here. The rest will both bore you and cost more than you're going to want to invest. To the rest of you, those that own businesses and want to sincerely make every effort to keep it safe, read on.
How would we do it?
You invest a lot of time working with a company like Twisted Networx and let us help you do it. You can't do it on your own. Sorry, but it's a fact. I can't perform my own MRI scans because I'm not a doctor. You can't truly maintain rock-solid backup systems and threat-test them against the latest technologies because you're not an IT engineer. Your in-house "computer guy" with a USB hard drive that's telling you he's got you covered is lying to you unless you're a VERY small business with one or two computers.
So, let's take this from the standpoint of an actual customer we have - the customer that inspired us to write this article for their staff. What would I do as their IT firm if I wanted to guarantee that we were literally doing everything possible to protect them while still allowing to do business the way they need to. (And getting off the internet isn't an option for most people in today's world because their vendors require an internet connection to utilize their services.)
They have the following:
- 1 server
- 4 mission critical workstations running proprietary databases for storing patient data in different formats, each with massive amounts of related imagery (because they're all x-ray related).
- 26 normal workstations
- 1 Fifty megabit internet cable connection with a 5 mb upload.
- Their data grows at a rate of about 25gb per year based on the past three years trends.
I'm not going to cover the how-to here. I'm just going to cover the part you'd need to know if you were the person I had to convince to absorb these costs per month.
We need to backup the server, both locally, and to the cloud, but because of the nature of ransomware and it's ability to remain undetected in a system, we need to be able to do a weekly snapshot going back at least a month, of the FULL data set. The dataset we have to work with is about 250 gb.
Then we need to backup the four xray platforms they use as well as ALL the Dicom imagery they generate through these programs. You can expect 100gb each currently, but need to plan on handling at least 500 gb each by the end of a year or two. That means so far we need to expect a solution that includes somewhere around 3 terabytes of local system imaging with hourly delta changes. Then we'd need basically an unlimited cloud-retention dataset to maintain data integrity as well as meeting the requirements for data storage required under other laws.
Knowing we're going to be backing up this much data to the cloud means we have to have an internet connection capable of uploading that much data without killing their network. Remember, we have four more mission critical machines to do this to as well.
The bill from Time Warner Cable to give them a sufficient upload speed will run around $600 a month. (Funny, I have that same package at home for $50 per month.) Let's assume that we locally collect the dataset the first time and ship it to the cloud provider via UPS. Waiting on the first-time dataset to seed would still take weeks otherwise.
- Collecting the initial dataset and shipping it off - $500 in time and labor.
- Purchasing the 3tb local NAS to handle the in-house copy of the data on a day-to-day basis: $2900.00
- Initial setup and testing of the solution: $1100.00
- Monthly cost of hosting and backing up an unlimited dataset: $600 a month, no contract.
Total upfront cost: $5,150.
Monthly cost (Cable internet at $600/month plus $600/month for backup): $1,200 per month
Some of you see that like I do - oh, that's not bad.
Others see it like a lot of small business owners do - "Holy crap! $14,000 a year for backup?! I have a USB drive that works just fine and it cost $200!"
The difference is in how much the two types of people perceive two things:
- How much they really believe a total network rebuild would affect their bottom line.
- How likely they think they are to be hit with something ransomware or cryptoware.
We try to look at it from both perspectives and try to help customers balance the cost against the need. Depending on your type of business, a solution like this might be affordable for you, or it might not. We cant' make that decision for you, nor do we want to. We can (and have) informed the world at large what's out there, how to avoid it the best you can, and how to defend against it if you choose to take stronger measures for defense.
The harsh and bitter truth is -your company's data and safety on the internet is in the hands of the LEAST intelligent person you have employed that has access to the internet.
Can we help with your needs?
Absolutely. If you've read everything above and are still serious about wanting to do the most you humanly can to prevent catastrophic damage to your computer systems (whether it be from ransomware or something like a fire in your offices), then we would love to help. We just want to set realistic expectations for customers before wasting our time or yours.
If you don't think it's worth spending a couple hundred dollars a month to protect your data integrity, then this article will save both you and our engineers a wasted phone call. If you are larger, and have more mission-critical systems, that monthly total goes up a little. If you are an enterprise customer, you most likely already have a solution in place but you just wanted to come here and read how the little guys do it. lol.
Either way, we thank you for taking the time to read this and we will gladly talk with you in detail about how you can protect your business or home computers. Give us a call or click on our Contact page to get in touch today.